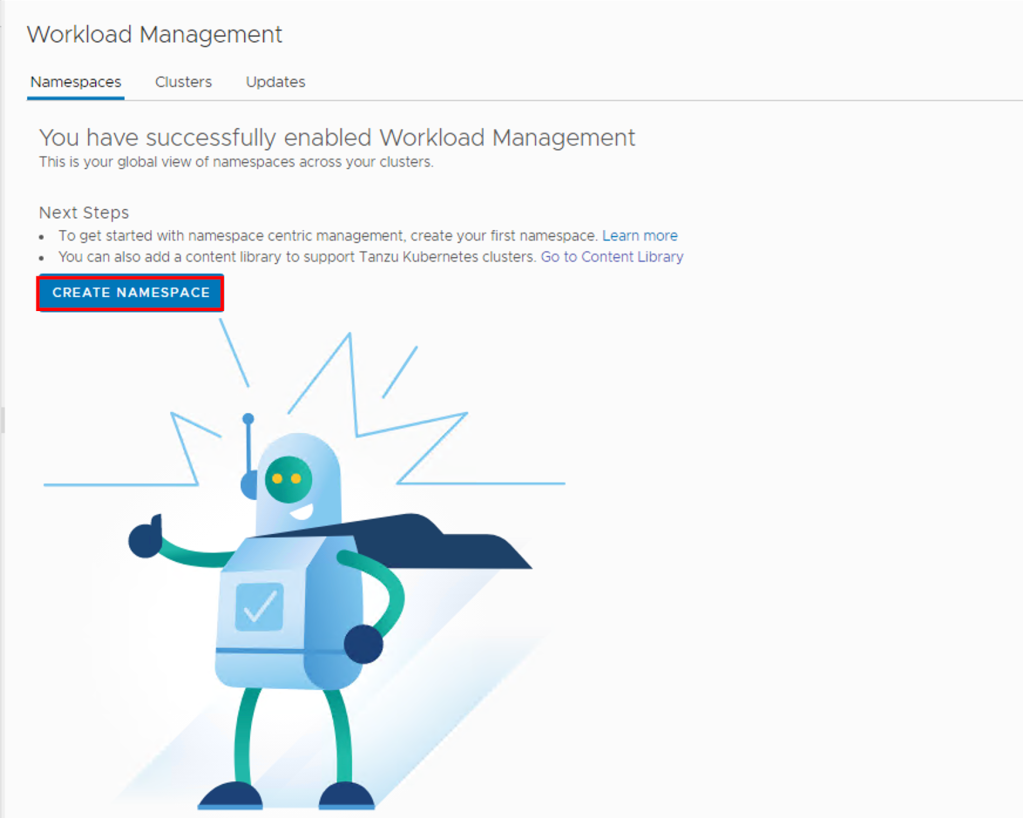
Secure remote access to the cloud services is essential to cloud adoption and use. Cloud Director based cloud allows every tenant to use a dedicated edge gateway, providing a simple and easy-to-use solution that supports IPsec site-to-site virtual private networks (VPNs) backed by VMware NSX-T. Since NSX-T today does not support SSL VPN and this limitation requires providers or tenants to select alternative solutions, including open source or commercial, depending on the desired mix of features and support. Example of such solutions are OpenVPN or Wireguard.
In this blog post we will deploy openVPN as a tenant admin to allow access cloud resources from Cloud using VPN Client.
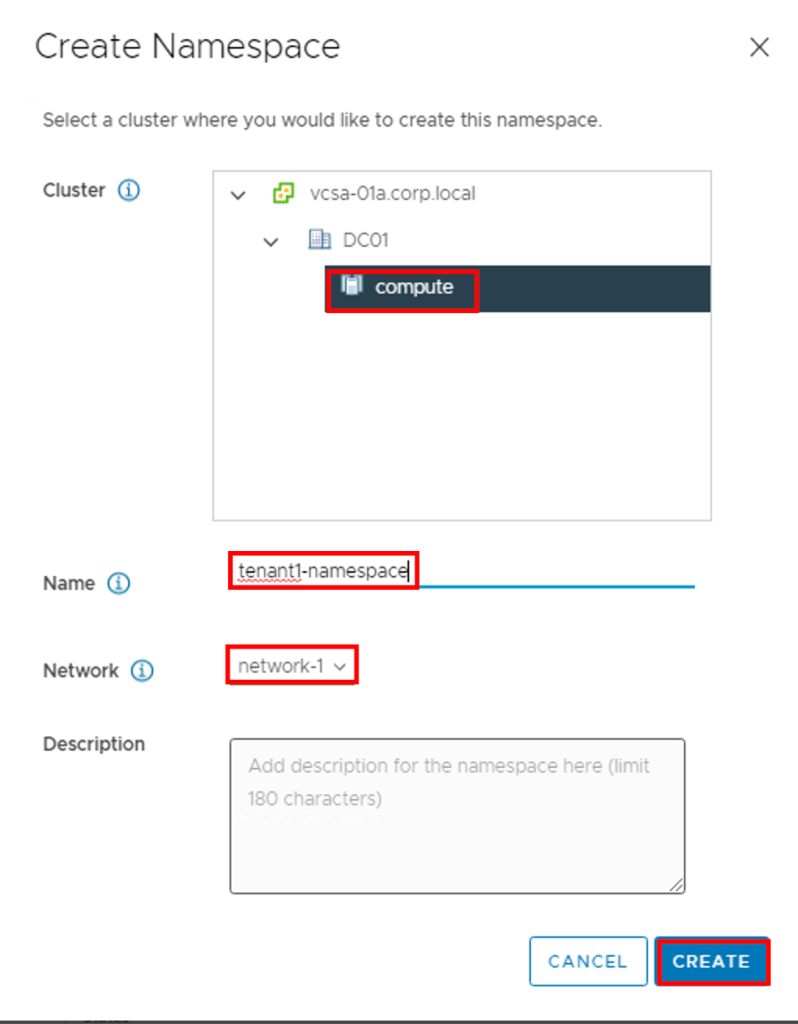
Create a new VDC network
Lets create a new routed Org VDC Network and we will deploy OpenVPN on this network, you can also deploy it on existing routed network.
- In Cloud Director go to Networking Section and Click on New to create a new router Network
- Select the appropriate Org VDC
- Select Type of Network as “Routed”
- Choose appropriate Edge for this routed network association
- Give the network an Gateway CIDR
- Create a pool of IPs for Network to allocate
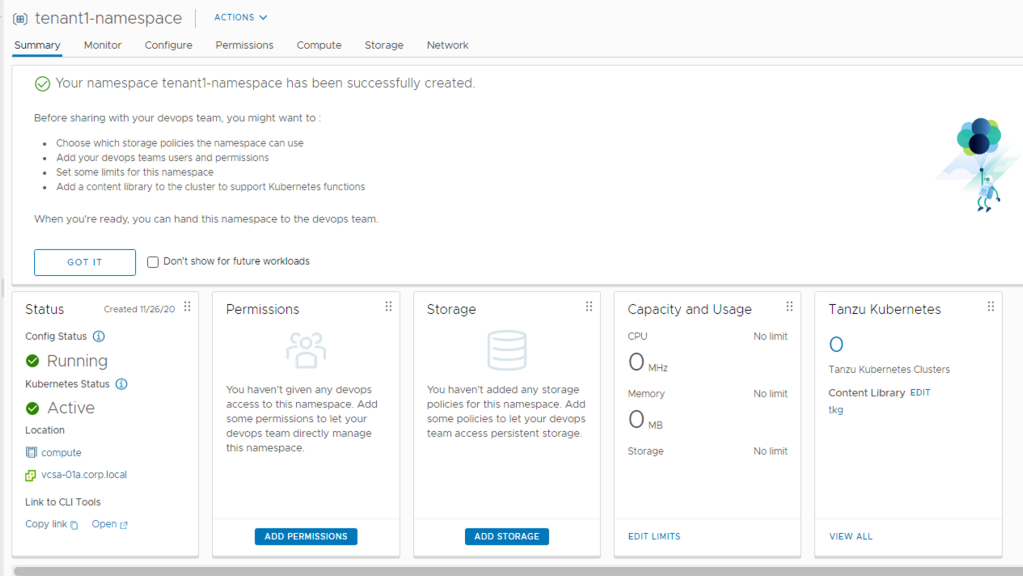
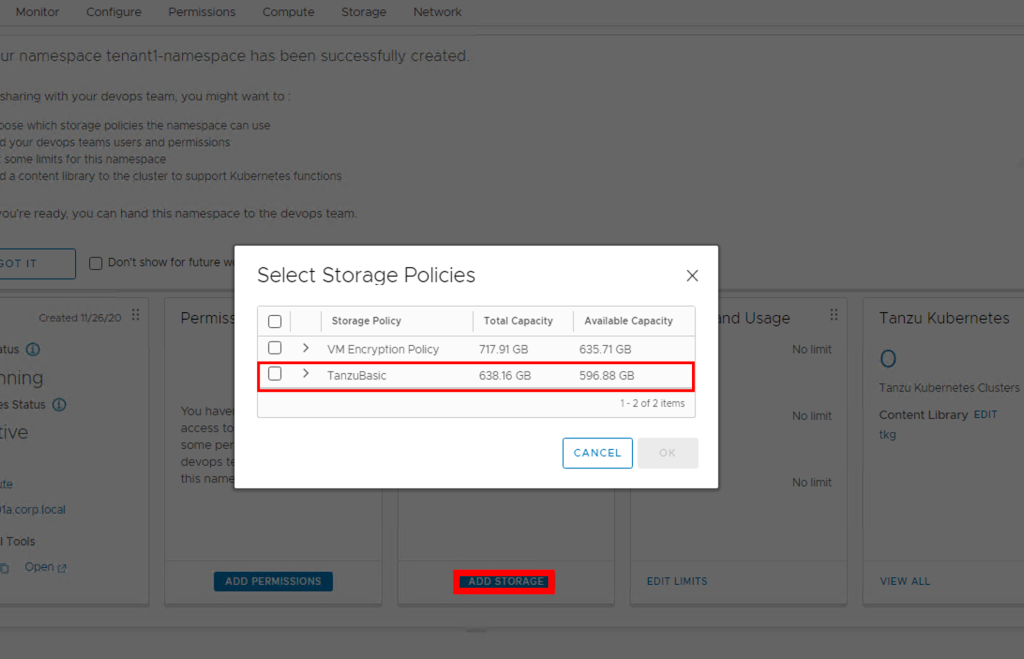
- check the summary and click finish to create a network a routed netwrok
Creating NAT Rules
After creating routed network, go on to Edge gateway and open the edge gateway configuration:

Create two NAT rules for OpenVPN appliance:
- SNAT rule to allow OpenVPN appliance out bound Internet access
- OpenVPN Appliance IP to one External IP
- DNAT rule to allow OpenVPN appliance Inbound access from Internet
- External IP to OpenVPN appliance IP

You might have to open certain firewall rules to access OpenVPN admin console which depend on from where you are accessing the console.
NAT for Cloud Director Services
Since Cloud Director Service is managed service and its architecture is different then cloud providers environment, so for CDS, we need to follow few extra steps as explained below:

Deploy OpenVPN Appliance
- I have downloaded the latest OpenVPN appliance from Here: -https://openvpn.net/downloads/openvpn-as-latest-vmware.ova
- I have uploaded in to a catalog , Select from Catalog and Click on Create vAPP

Provide a Name and Description

Select the Org VDC

Edit VM configuration

This is very important step , make sure you choose:
- Switch to the advance networking workflow
- Change IP assignment to “Manual“
- assign a valid IP Manually from the range which we had created during network creation, if you are not putting IP here then on appliance you need to struggle for IP assignment etc..

Review and finish, This will deploy the OpenVPN appliance, once deployed power on the appliance. Now time to configure the appliance…
OpenVPN Initial Configuration
In VMware Cloud Director go to Compute and click on Virtual Machines and open the console of your OpenVPN virtual machine.

Log in to the VM as the root user and for Password – Click on “Guest OS Customization” and click on Edit

Copy the password which is in the section “Specify password“, and use this password to login to OpenVPN virtual machine

After login, you will be prompted to answer few questions:
Licence Agreement: as usual , you do not have choice, Enter “yes”

Will this be the primary Access Server node?: Enter “Yes”

Please specify the network interface and IP address to be used by the Admin Web UI: If the guest customizations were applied correctly, this should default to eth0, which should be configured with an IP address on the network you selected during deployment.

Please specify the port number for the Admin Web UI: Enter your desired port number, or accept the default of 943.

Please specify the TCP port number for the OpenVPN Daemon: Use default “443”

Should client traffic be routed by default through VPN?: Choose “No”.
if you enter “yes”, it will not allow client device from accessing any other networks while the VPN is connected.
Should client DNS traffic be routed by default through the VPN?: Choose “No” if your above answer is “No”.
Use local authentication via internal DB? : Enter Yes or No based on your choice of authentication.
Should private subnets be accessible to clients by default? : Enter “yes” this will enable your cloud networks accessible via the VPN.
Do you wish to login to the Admin UI as “openvpn”?: Answer “yes” which will create a local user account named as “openvpn” If you answer no, you’ll need to set up a different user name and password.

Please specify your Activation key: If you’ve purchased a licence, enter the licence key, otherwise leave this blank.

If using default “openvpn” account, after installing the OpenVPN Access Server for the first time, you are required to set a password for the “openvpn” user at the command line interface with the command “#passwd openvpn” and then use that to login at the Admin UI. This completes the deployment of appliances, now you can browse the config page, on which we will configure SSL VPN specific Options:

This section shows you whether the VPN Server is currently ON or OFF. Based on the current status, you can either Start the Server or Stop the Server with the button you see there.

Inside VPN Network settings , specify network settings which applies to your configuraiton.

Create users or configure Other authentication methods, i am creating a sample user to access cloud resources based on the permissions.

Tenant User Access
Tenant user access public IP of SSL VPN that we had assigned initially and login with credentials

Once Login , User has choice to download the VPN Client as well as Connection profiles , these connection profiles will have login information for the user.

Incase if user sees private IP in profile, (@192.168.10.101), then click on pen icon to edit the profile


Once user has edit the profile, he can successfully connect to Cloud.

While Label OpenVPN
In case provider wants to while label the OpenVPN, he can easily do this by following the simple procedure:
- Copy an Logo to OpenVPN appliance and edit file – nano /usr/local/openvpn_as/etc/as.conf
- Add below line after #sa.company_name line for company logo
- sa.logo_image_file=/usr/local/openvpn_as/companylogo.png
- uncomment sa.company_name and change it to your specific text desired for Company Name for changing company name
- To hide footer, below the sa.company_name and/or sa.logo_image_file variables, add the following:cs.footer=hide
- Save and exit the file, then restart the OpenVPN Access Server:service openvpnas restart

This completes the installation/configuration and white Labelling of the OpenVPN and these configure steps applies to VMware Cloud Director and Cloud Director service’s tenant portal on VMware Cloud on AWS, Please share feedback if any.