Cloud Director VDCs come with all the features you’d expect from a public cloud, Virtual Data Center is a logical representation of a physical data center, created using virtualization technologies and a virtual data center allows IT administrators to create, provision, and manage virtualized resources such as servers, storage, and networking in a flexible and efficient manner. Recently released new version of VMware Cloud Director 10.4.1 released quite a lot of new features. In this article I want to double click on to external networking…
External Networks
An external network is a network that is external to the VCD infrastructure, such as a physical network or a virtual network, external networks are used to connect virtual machines in VCD with the external world, allowing them to communicate with the Internet or with other networks that are not part of the VCD infrastructure
New Features in Cloud Director 10.4.1 External Networks
With the release of Cloud Director 10.4.1, External networks that are NSX-T Segment backed (VLAN or overlay) can now be connected directly to Org VDC Edge and does not require routed through Tier-0 or VRF the Org VDC Gateway is connected to. This connection is done via the service interface on the service node of the Tier-1 GW that is backing the Org VDC Edge GW. The Org VDC Edge GW still needs a parent Tier-0/VRF although it can be disconnected from it. here are some of the use cases some of the use cases of the external network we are going to discusses…
- Transit connectivity across multiple Org VDC Edge Gateways to route between different Org VDCs
- Routed connectivity via dedicated VLAN to tenant’s co-location physical servers
- Connectivity towards Partner Service Networks
- MPLS connectivity to direct connect while internet is accessible via shared provider gateway
Security VDC Architecture using External Networks (transit connectivity across two Org VDC Edge Gateways)
A Security VDC is a common strategy for connecting multiple VDCs and security VDC become single egress and ingress points as well as can deploy additional firewall etc, in below section i am showing how that can be achieved using new external network feature:
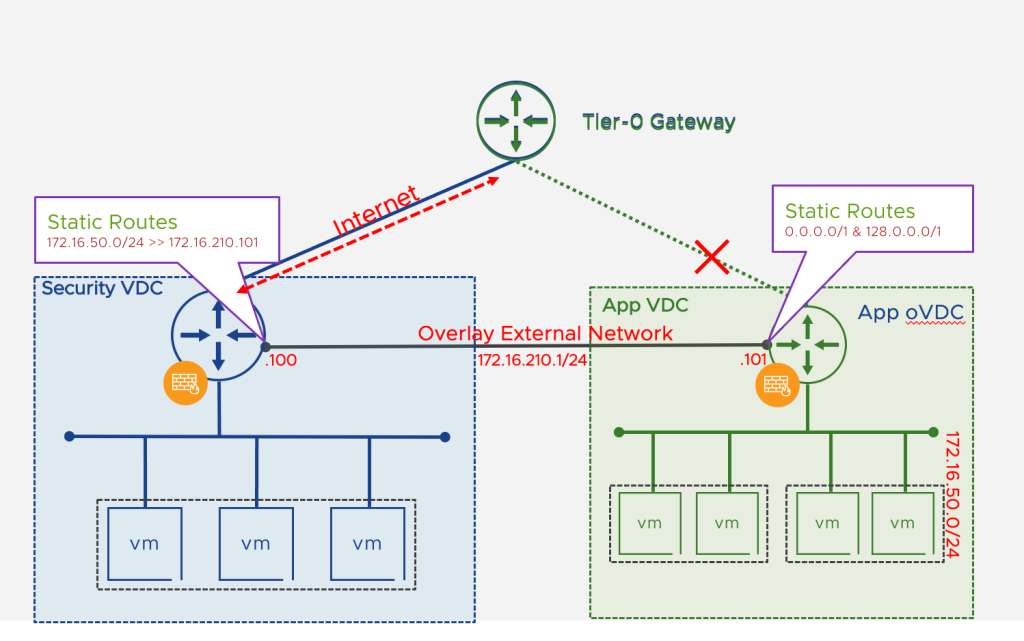
- This is using Overlay (Geneve) backed external network
- This Overlay network must be prepared by provider in NSX as well as in Cloud Director
- NSX Tier-1 GW does not provide any dynamic routing capabilities, so routing to such network can be configured only via static routes
- Tier-1 GW has default route (0.0.0.0/0) always pointing towards its parent Tier-0/VRF GW
- Set default route to the segment backed external network you need to use two more specific routes. For example:
- Ø0.0.0.0/1 next hop <IP> scope <network>
- Ø128.0.0.0/1 next hop <IP> scope <network>
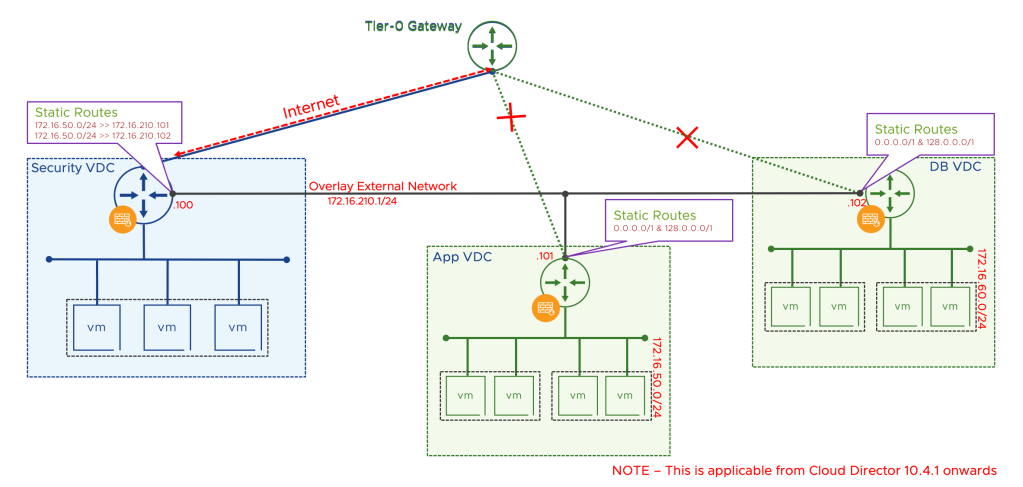
Security VDC Architecture using External Networks – Multi-VDC
- Log in to the VMware Cloud Director Service Provider Admin Portal.
- From the top navigation bar, select Resources and click Cloud Resources.
- In the left pane, click External Networks and click New.
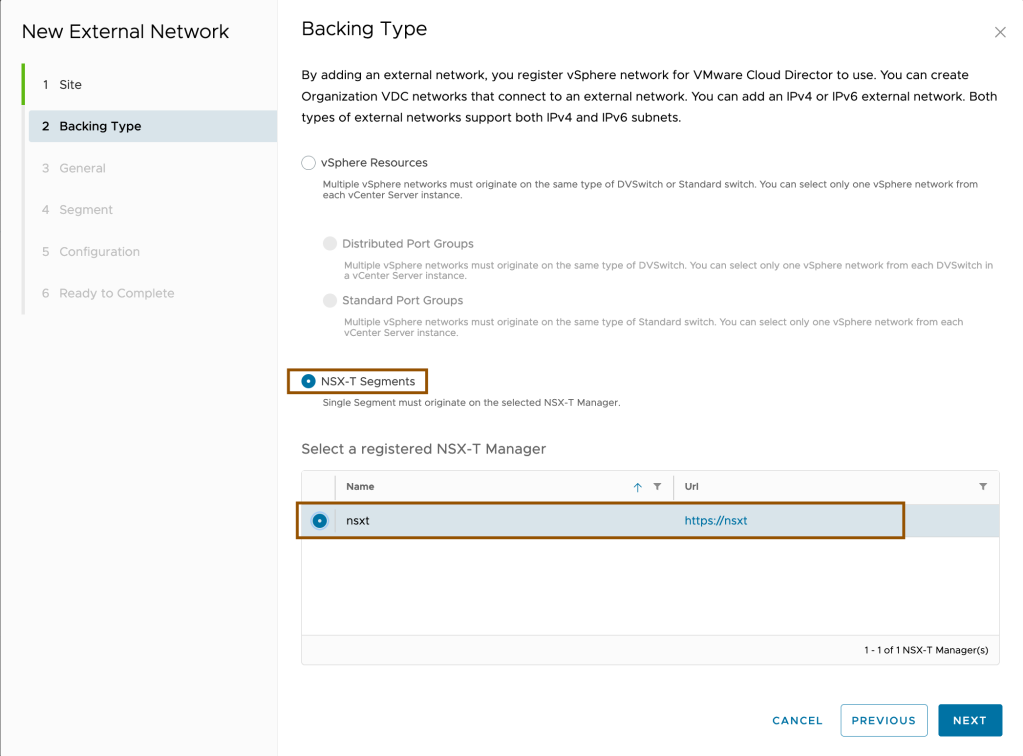
On the Backing Type page, select NSX-T Segments and a registered NSX Manager instance to back the network, and click Next.
Enter a name and a description for the new external network
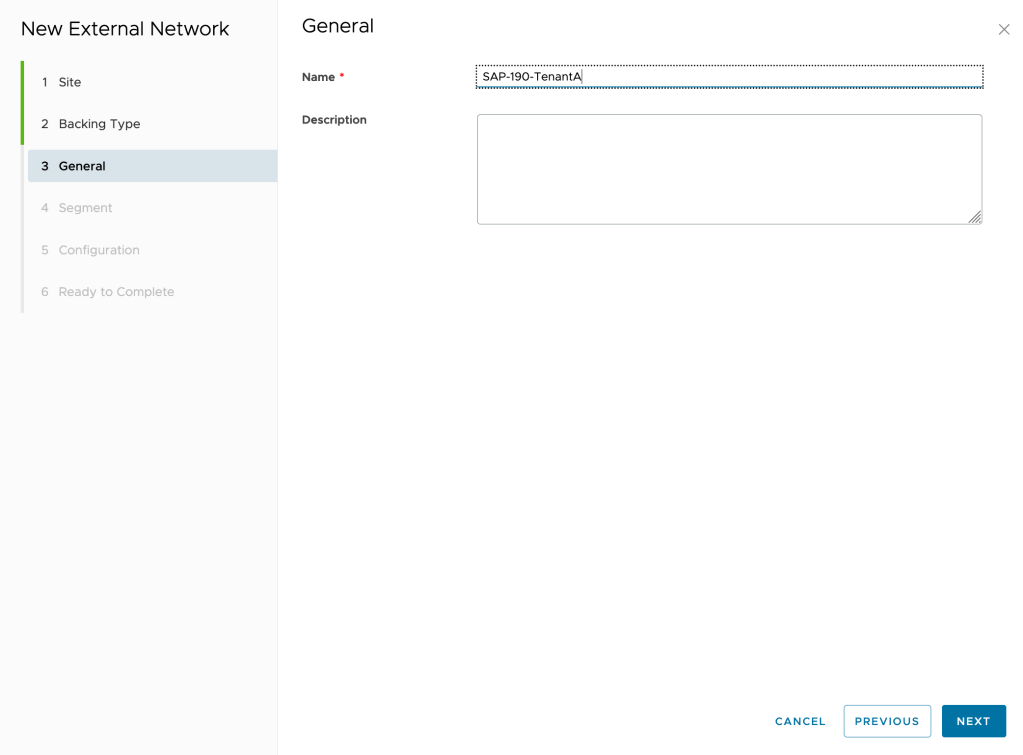
Select an NSX segment from the list to import and click Next. An NSX segment can be backed either by a VLAN transport zone or by an overlay transport zone
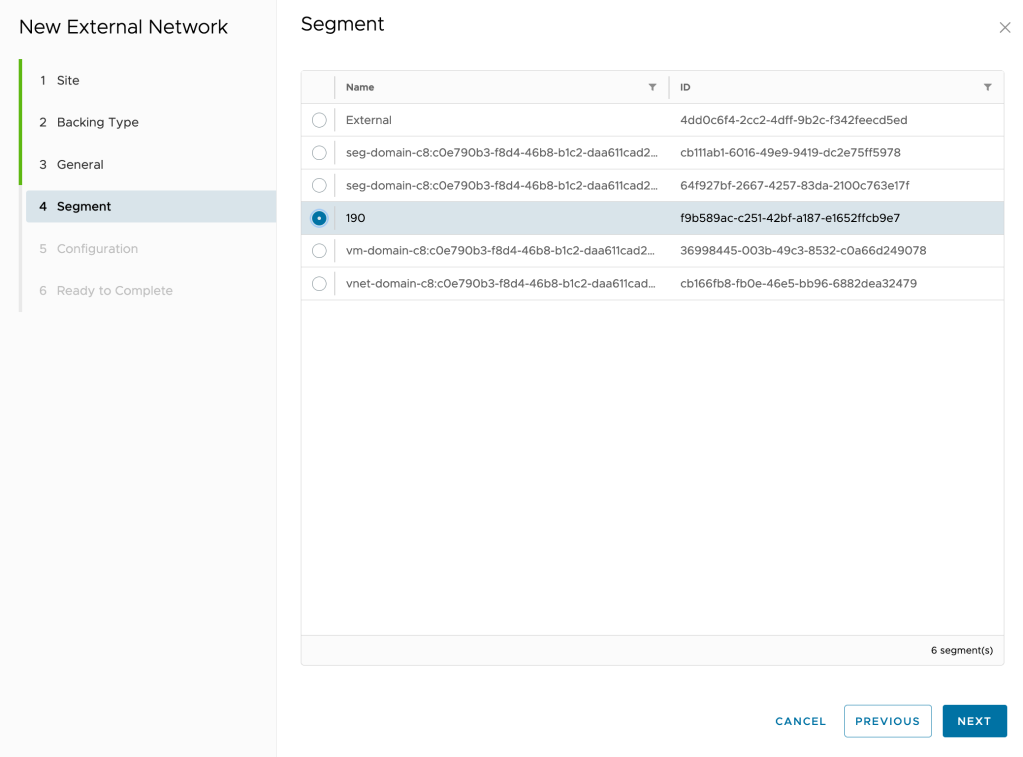
- Configure at least one subnet and click Next.
- To add a subnet, click New.
- Enter a gateway CIDR.
- To enable, select the State checkbox.
- Configure a static IP pool by adding at least one IP range or IP address.
- Click Save.
- (Optional) To add another subnet, repeat steps Step A to Step E.
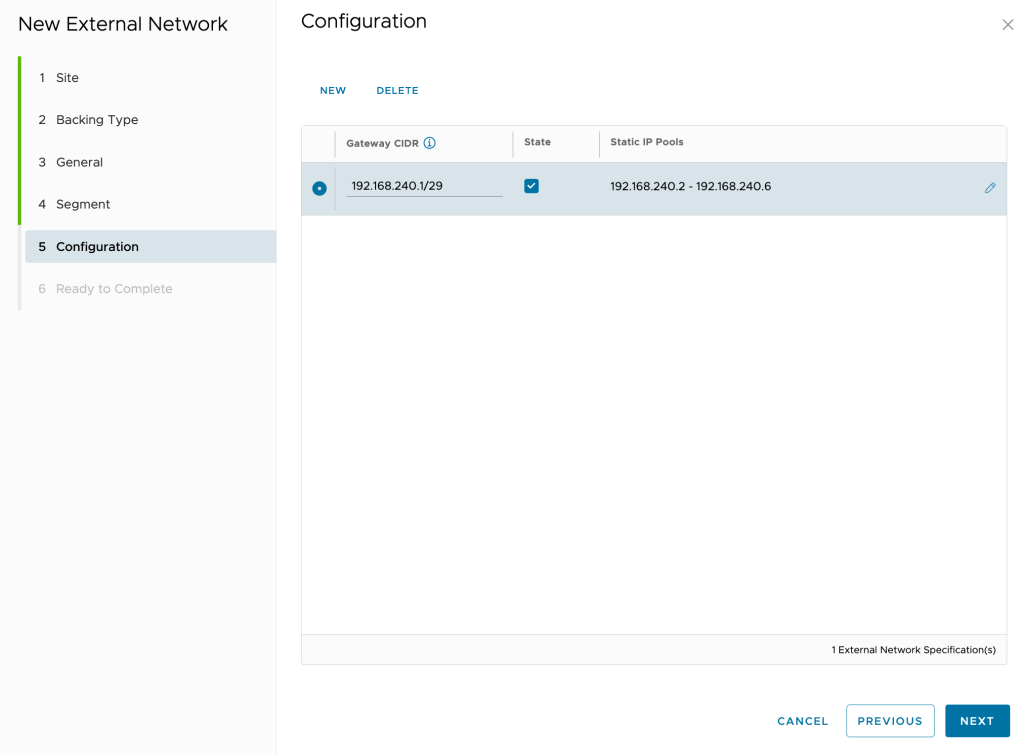
Review the network settings and click Finish.

Now provider will need to go to tenant org/vdc and add above configured external network in to tenant tier1 edge and offer net new networking configuration and options.
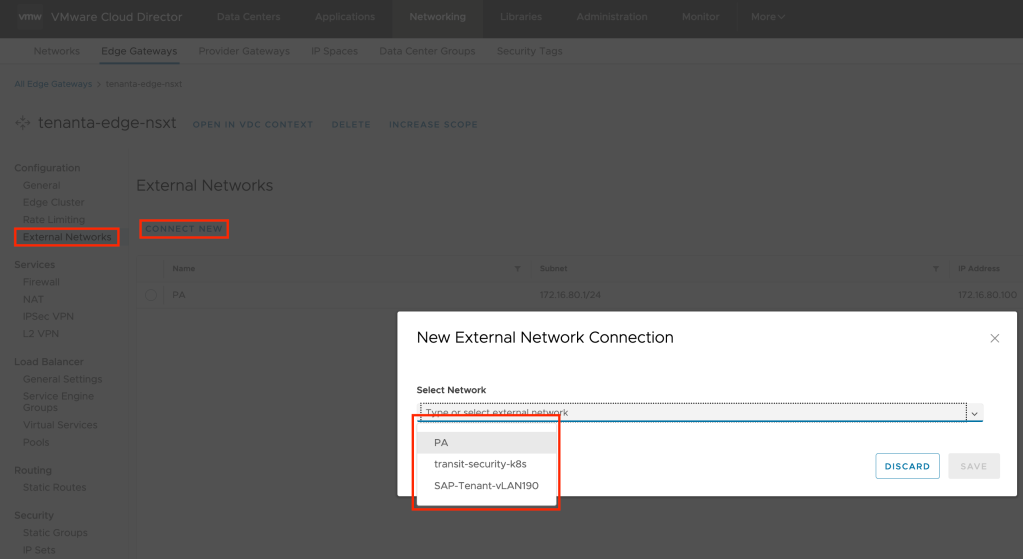
Other Patterns
Routed connectivity via dedicated VLAN to tenant’s co-location physical servers or MPLS
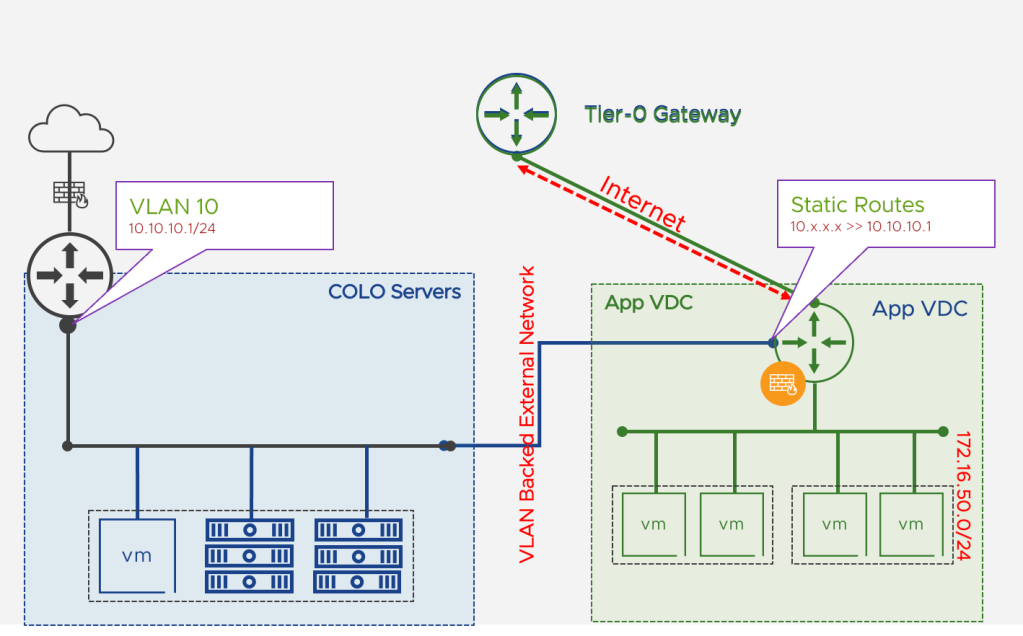
- This is using vLAN backed external network
- This vLAN backed network must be prepared by provider in NSX as well as in Cloud Director
- NSX Tier-1 GW does not provide any dynamic routing capabilities, so routing to such network can be configured only via static routes
- One VLAN segment, it can be connected to only one Org VDC Edge GW
- Tier-1 GW has default route (0.0.0.0/0) always pointing towards its parent Tier-0/VRF GW
- Set default route to the segment backed external network. For example:
- Ø172.16.50.0/24 next hop <10.10.10.1> scope <external network>
Connectivity towards Partner Service Networks

- This is using vLAN backed external network
- This vLAN backed network must be prepared by provider in NSX as well as in Cloud Director
- NSX Tier-1 GW does not provide any dynamic routing capabilities, so routing to such network can be configured only via static routes
- One VLAN segment, it can be connected to only one Org VDC Edge GW
- Tier-1 GW has default route (0.0.0.0/0) always pointing towards its parent Tier-0/VRF GW
- Set static route to the segment backed external network you need to use two more specific routes. For example:
- Ø<Service Network> next hop <Service Network Router IP> scope <External Network>
DOWNLOAD PDF from Here
i hope this article helps providers offer net new additional network capabilities to your tenants. please feel free to share feedback.
